Proxmox: Nextcloud into an unprivileged LCX container with a mounted SMB as Data folder
(Last Updated On: )Disclaimer: I am a noob doing complex stuff in Proxmox here.Do this at your own risk. I give no warranty. DO A BACKUP FIRST!
Step 1: Create the Nextcloud LXC container
This is the easy part, Proxmox already has a Nextcloud LXC template container. Just to be 100% sure we have it, we will update the templates list going to the host shell and running:
pveam updateNow we can go to the Proxmox storage where our templates are saved (usually local-pve), there select CT Templates -> Templates, search and download the Nextcloud template.
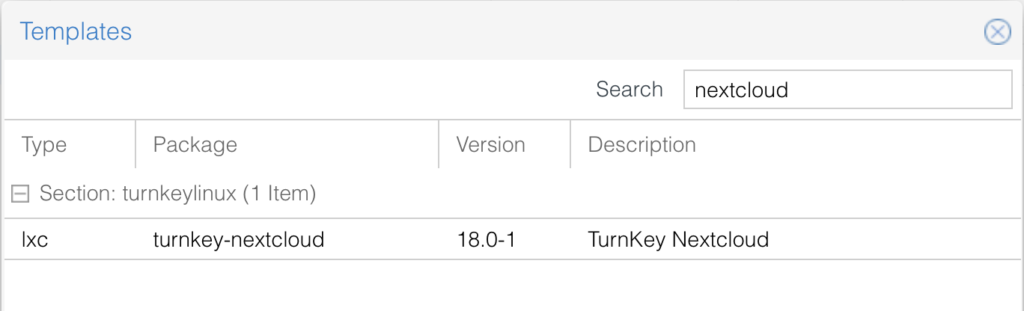
With the template downloaded, we can proceed to create the new container, remember to write the root password in a secure place!
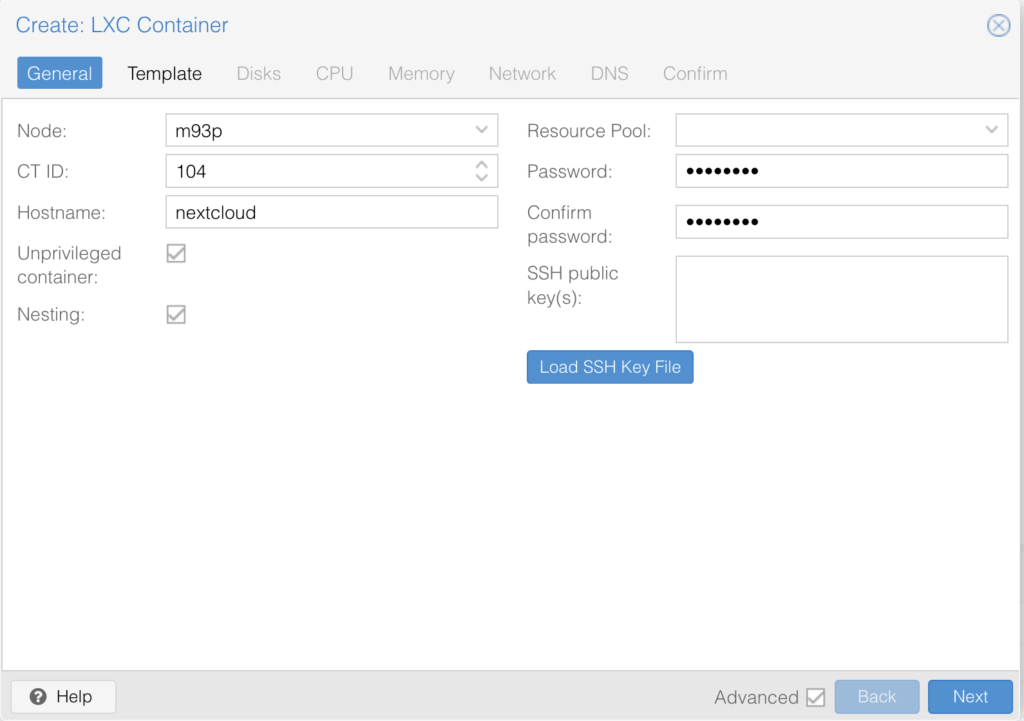
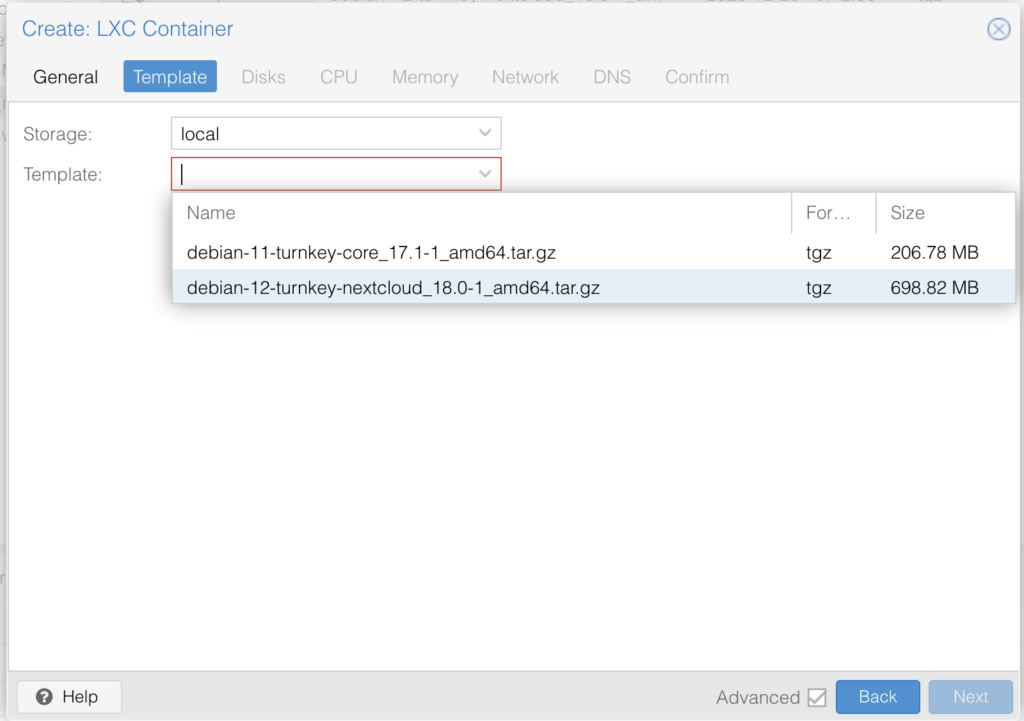
The rest of the options had to be adjusted to your requirements, check the server requirements for Nextcloud on the official website. If you give a manual IP write it down.
Now start the container and open the shell, put root as the user and the password you set for the container.
After the installation of the updates, put the IP of your container (or the hostname if using one) in the domain field in the Nextcloud installation setup. You can always add other hostnames, even external ones, later. Also the required passwords. After reboot, your Nextcloud instance should be running on the given IP/hostname.
Step 2: Mount the SMB/CIFS storage
We can not use the Proxmox UI for this because we do not get any option as to what to choose for the uid and gid. They are always mapped to the proxmox’s root user, and we need to map it to the Nexcloud container’s www-data user.
On the Node Proxmox shell, create a file for the credentials. I will use .nextcloud_smb_credentials
touch ~/.nextcloud_smb_credentialsWith the editor of your preference (vi or maybe nano), write your smb storage credentials:
username=nextcloud_user
password=super_secret_password_123As extra security, set it the read/write access for just the root user:
chmod 700 ~/.nextcloud_smb_credentialsWe also need to create the folder that will serve as a mount point, in my case, the mount folder will be inside nas-one and named nextcloud.
mkdir /mnt/nas-one
mkdir /mnt/nas-one/nextcloudNow we are ready to update our fstab file with the needed information to mount our SMB storage assigning the uid and gid to the www-data user. In my installation, www-data had the uid 33, which mapped to the host container would translate to 100033 (Guest UID/GID + 100000) . Also it is important to set the permissions to 770, otherwise it will not work.
nano /etc/fstab//x.x.x.x/path-to-my-smb-folder /mnt/nas-one/nextcloud cifs credentials=/root/.nextcloud_smb_credentials,uid=100033,gid=100033,dir_mode=0770,file_mode=0770 0 0Here a description of this command:
//x.x.x.x/path-to-my-smb-folder: This is the network location (SMB/CIFS share) you want to mount. Replacex.x.x.xwith the actual IP address, andpath-to-my-smb-folderwith the specific path to the shared folder./mnt/nas-one/nextcloud: This is the local mount point where the remote SMB/CIFS share will be mounted. Adjust the path according to your system’s directory structure.cifs: This specifies the filesystem type, indicating that it’s a Common Internet File System (CIFS) share, which is a network file-sharing protocol.credentials=/root/.nextcloud_smb_credentials: This option specifies the location of a file containing the credentials (username and password) required to access the SMB/CIFS share. In this case, the credentials file is located at/root/.nextcloud_smb_credentials. Make sure this file has appropriate security permissions to protect sensitive information.uid=100033,gid=100033: These options set the user and group ownership of the mounted files and directories. In this example, both the user (uid) and group (gid) are set to the numeric identifier 100033. Adjust these values based on your system’s user and group IDs.dir_mode=0770,file_mode=0770: These options set the permissions for directories (dir_mode) and files (file_mode) on the mounted share. The octal values0770indicate that the owner and group have read, write, and execute permissions, while others have no permissions.0 0: These are the options for dump and pass. In most cases, these are set to0, indicating that the filesystem should not be backed up and should not be checked during system boot.
Finally, we bind it to our Nextcloud LXC container editing the container config
nano /etc/pve/lxc/<container_id>.confadding:
mp0: /mnt/nas-one/nextcloud,mp=/mnt/nas-one/nextcloudDo not forget to activate the new mount using:
systemctl daemon-reload && mount -aOr if that does not work
mount -vvv /mnt/nas-one/nextcloudStep 3: Move the data folder to your NAS.
On the LXC Container shell run the following commands:
# go to maintenance mode
runuser -u www-data -- php /var/www/nextcloud/occ maintenance:mode --on
# copy the existing data to it’s new location
runuser -u www-data -- cp -r /var/www/nextcloud/data/. /mnt/nas-one/nextcloud/data
# create an .ocdata file
runuser -u www-data -- touch /mnt/nas-one/nextcloud/data/.ocdata
# set your new data location.
runuser -u www-data -- php /var/www/nextcloud/occ config:system:set datadirectory --value=/mnt/nas-one/nextcloud/data
# disable maintenance
runuser -u www-data -- php /var/www/nextcloud/occ maintenance:mode --offCheck your Nextcloud instance. It should work as expected.
Optional: You can now delete /var/www/nextcloud/data if you are 100% sure all the data was transferred correctly.
Step 4:
Profit.



Hi Saninn, Thank you so much for this guide. I was tearing my hear out for three days trying to get a Proxmox unprivileged LXC to be able to write to a SMB/CIFS share on a Synology NAS. Other guides have gotten me quite close, e.g. I could read/write to… Read more »
I am glad it helped you! I am pretty sure I myself will need this information in a couple of months when I break something 😀
Thanks, good info. I had to reboot the Nextcloud container before Step 3, line 6 would work.